Just as I was getting ready to post an introduction to using LetsEncrypt on CloudFront and scheduling renewals with Lambda, AWS released a new service: AWS Certificate Manager or ACM. ACM issues SSL certificates, handles renewal automatically, and replaces existing certs.
Last week, I wrote about getting alerts for expiring SSL certs on your CloudFront distributions. If you switch to ACM, you can skip setting up that particular function. You can now set up certificates in the AWS console, and if you’re observant you’ll notice this page is served with an ACM certificate.
How Does it Work?
AWS Certificate Manager replaces your SSL certificate authority (Verisign, Komodo, GoDaddy, GlobalSign) and issues certificates automatically to customers with an AWS account. This makes it easier (and cheaper) to serve your site over SSL, because you don’t have to upload certificates or go through third-party verification. Amazon verifies your domain ownership and issues the certificate straight into your AWS account.
Here’s how it works:
- You put in the domain(s) that you need the SSL certificate for in the console
- Amazon sends a verification email to administrative addresses (e.g.
admin@yourdomain.com) - You receive the email and click through to confirm you own the domain.
- The certificate is granted, and you can now use it in CloudFront or Elastic Load Balancer
Did I mention the certs are free, renew themselves automatically, and the private key is safely stored in AWS Key Management Service (KMS), so only services with permission to use the cert can access the key? Certificates are 2048-bit RSA, and renew every 30 days.
Free, But is There a Catch?
There is a catch. Certificates are free, but you can’t use ACM-issued SSL certificates on any public IP address that isn’t Amazon-controlled. You’ll end up paying for your CloudFront or ELB costs, but you can cross “SSL certificate renewal” off your to-do list.
The ACM certificates also don’t provide Extended Validation (EV). With EV SSL, your organization name shows up in the URL bar. This is supposed to improve user confidence that they’re in the “right place.”
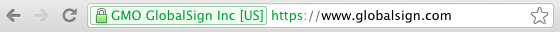
If you have that now, you’ll have to stick with your current certificate provider and wait until (maybe) AWS adds Extended Validation in the future.
The last catch is that the service only allows 20 certificates per year, and is available only in the us-east-1 region.
Wrapping up
What’s still not hot about the CloudFront/ACM setup? The 20 minutes it takes to roll out the cert.
What a whiner, right?
Thanks for reading. If you’ve got any CloudFront or ELB endpoints that don’t have SSL, you’re out of excuses.
To learn more you can read the service announcement, follow the “Getting Started” instructions in the documentation, then use the ACM Console to deploy your certificates.
Since setting up ACM (unlike LetsEncrypt) requires email to be set up for the domain being certified, you can now email ryan@serverlesscode.com with questions, comments, and suggestions. I look forward to hearing from you!
Did you like this post? Get more like it by signing up for RSS updates.